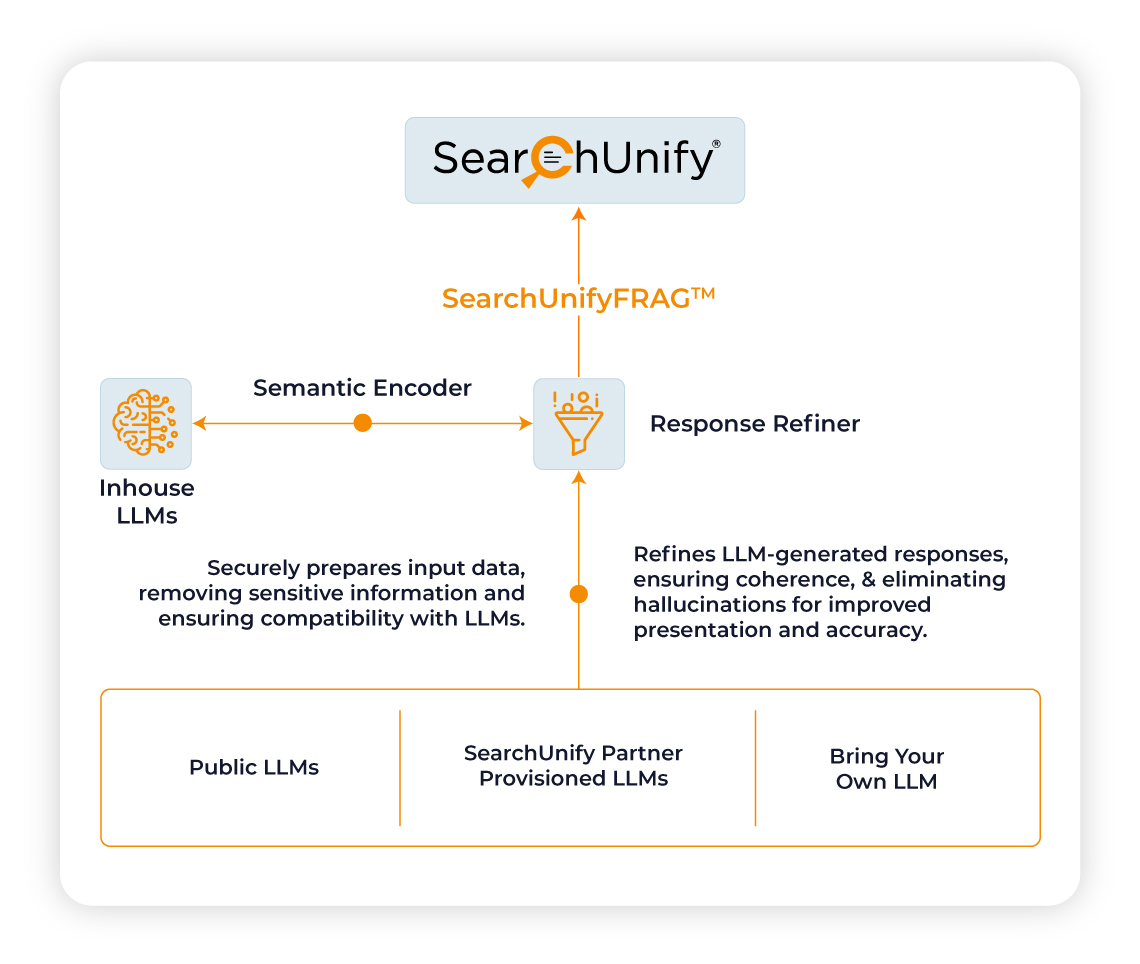
When integrating with third-party or in-house LLMs, SearchUnify implements robust security measures to safeguard your data and prevent decision bias:
Data Compatibility: Our Semantic Encoder ensures seamless data compatibility with LLMs while maintaining data integrity.
Sensitive Data Removal: We meticulously remove critical or sensitive information from the data before sending it to third-party LLMs.
Response Refinement: Our Response Refiner analyzes LLM-generated responses to ensure they are free from sensitive information and present only relevant, contextually appropriate knowledge to your users.
SearchUnify's parent company, Grazitti Interactive, has achieved regulatory compliance with ISO 27001:2013, HIPAA, ISO 27701:2019, and SSAE 18. SOC 1 and SOC 2 reports are available to customers upon request, and our SOC 3 report is publicly accessible. Your data is in safe hands.
SearchUnify is built for reliability and peace of mind
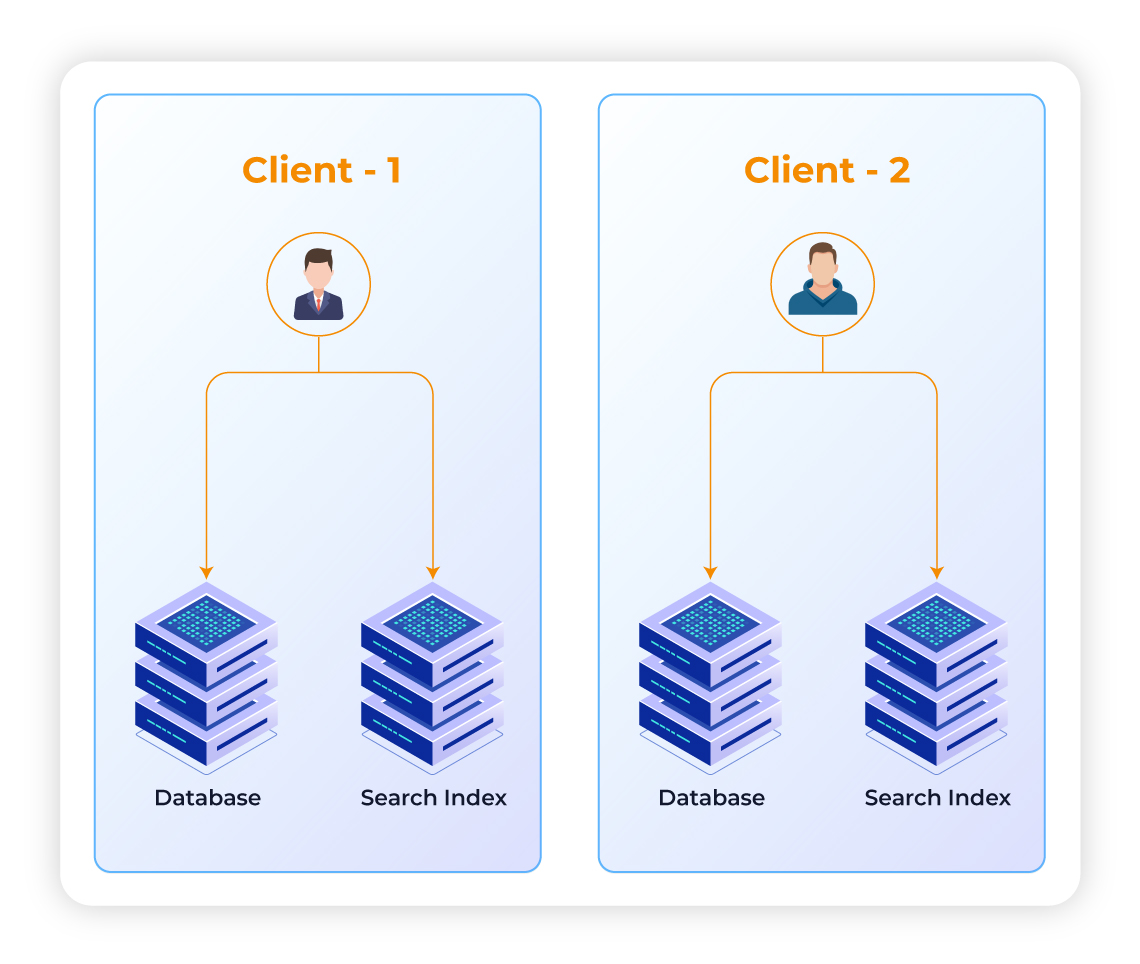
We utilize industry-standard OAuth 2.0 for secure authentication across different content source platforms. This ensures native installation and respects object and field-level access.

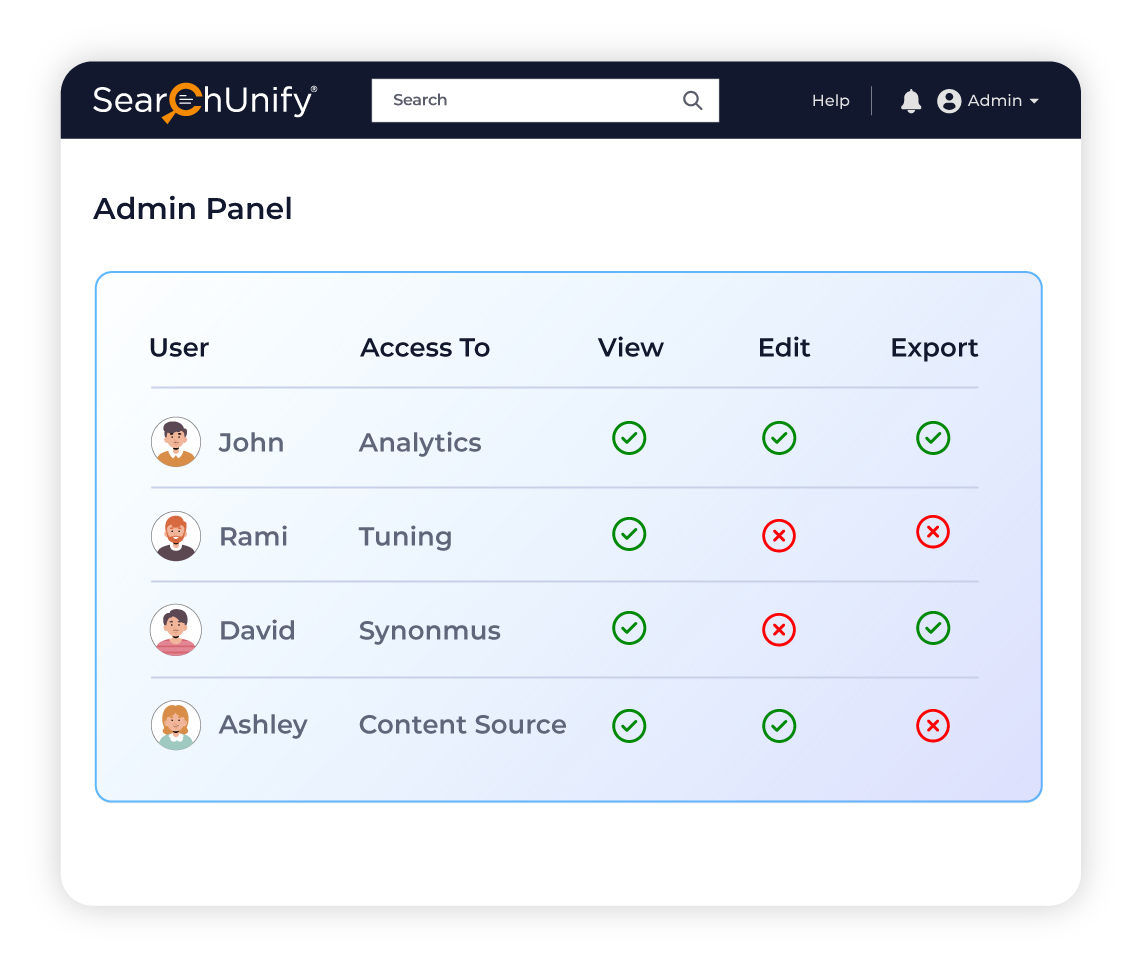
Define granular access permissions for different user roles within your SearchUnify instance. Whether it's through our UI, API, or other methods, you can easily manage who has access to what information.
Super Admin: Full control over the instance, including adding or removing users and modifying access settings.
Admin: Can manage moderator access and permissions.
Moderator: Limited permissions defined by the Admin.




incidents of data breach and downtime experienced by almost all our clients

factor score awarded by global leader in cybersecurity ranking, Security Scorecard
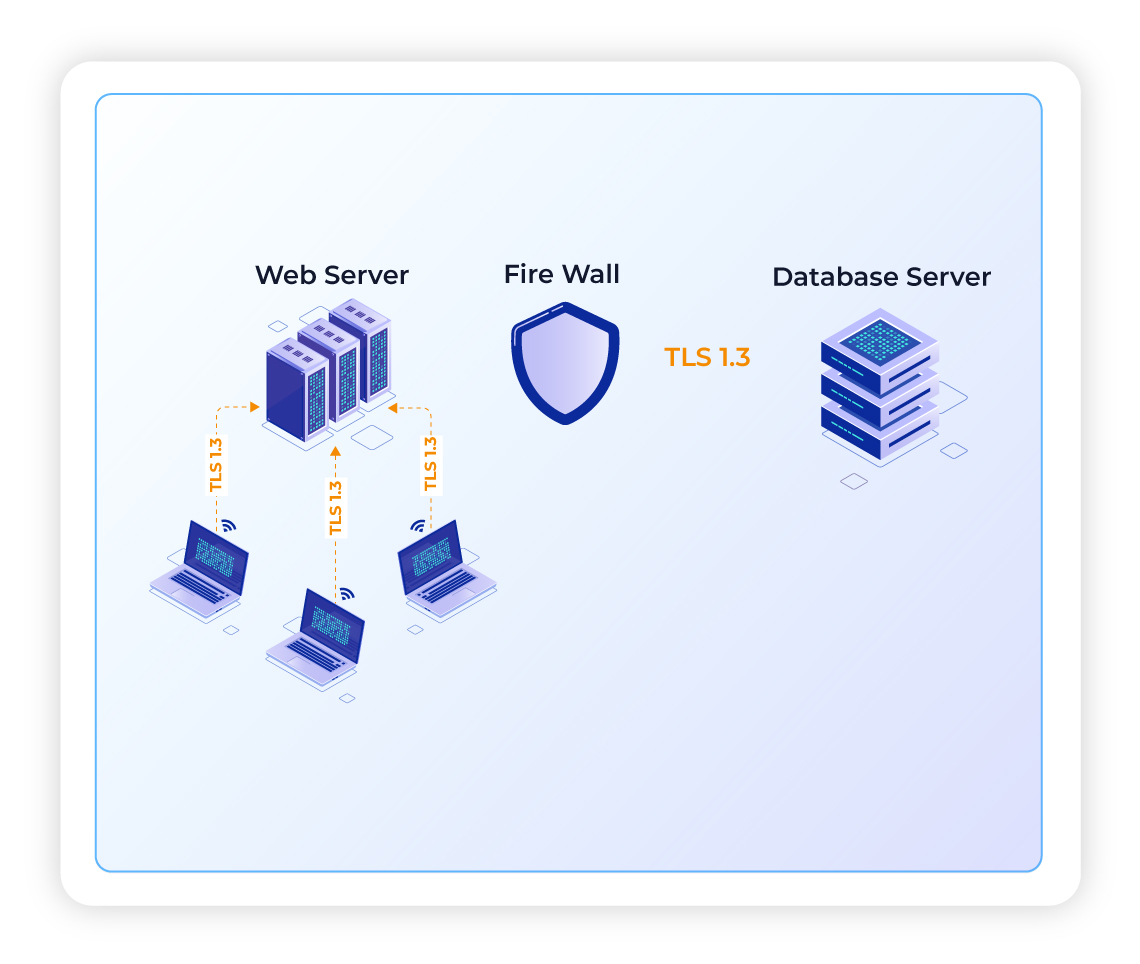
We employ Amazon EBS encryption and AES-256 encryption to protect your data at rest. For data in transit, we utilize TLS 1.3 and IPSEC VPN tunnels to safeguard against unauthorized access.
SearchUnify is built for reliability and peace of mind
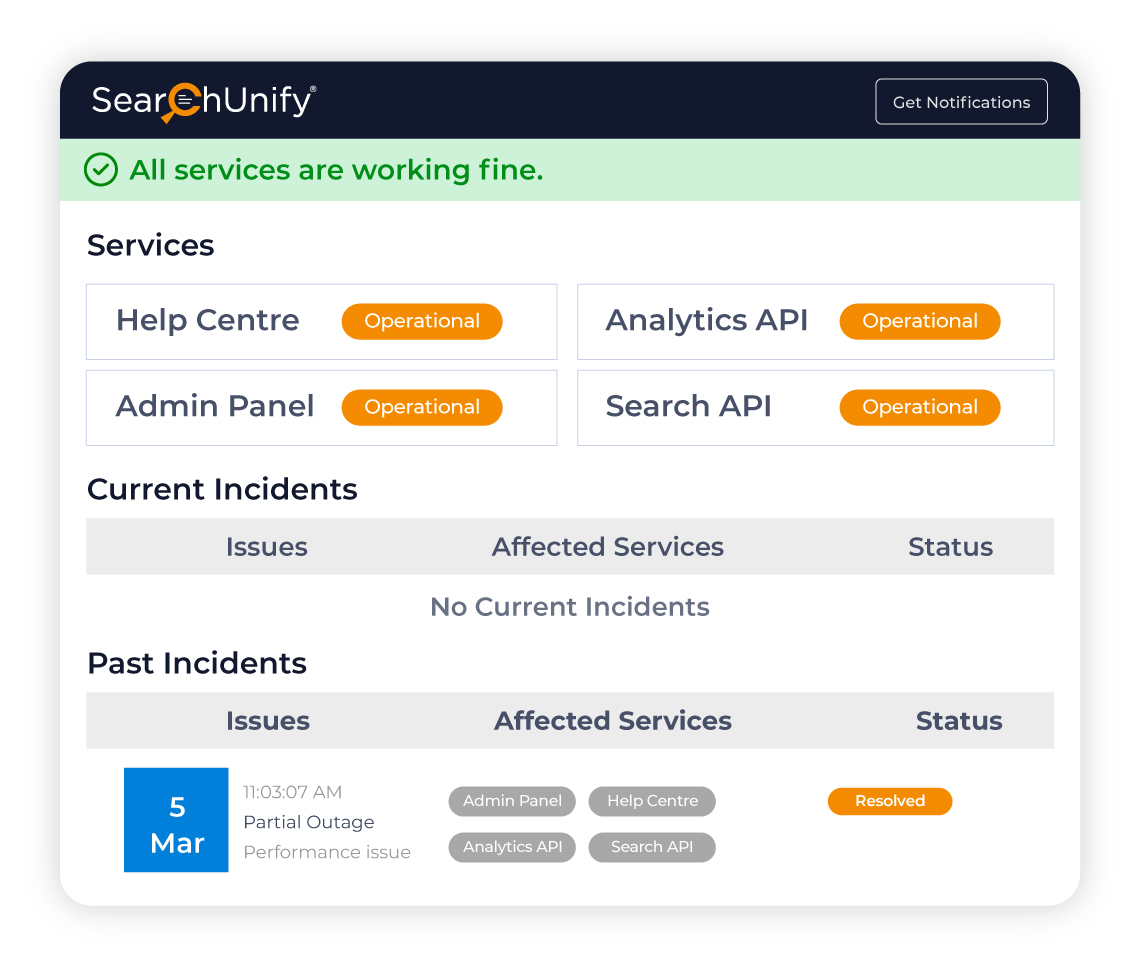
Stay informed about your SearchUnify instance's health with our dedicated Status Page. It provides real-time updates on the operational status of your admin panel, help center, content & search API. Automatic alerts are sent to administrators via phone or email in case of any errors or malfunctions.
SearchUnify undergoes regular Vulnerability Assessment and Penetration Testing (VAPT), both internal and external, to ensure our products meet the highest security standards. Our Customer Agreement prohibits unauthorized security testing on our platform without prior permission.
Know the latest trends and best practices in customer support